How To Secure Your E-mail in 5 Easy Steps
Email is the most used communications medium for business and for many of us at home too. We send SMS by the billion when we are on the move but email is still a firm favorite from the office or home. With more threats to our identity than ever, I thought it about time that we covered how to protect your email. That’s what prompted ‘How to secure your email in five easy steps’.
We all use email. Some of us depend on it for our livelihoods. We send invoices, vacation photos, login details, payment details, contracts and all kinds of private information via email without really thinking about its security. Very few people outside IT will ever consider just how much information they share via email, in the open, over the internet. Few people outside IT know how to truly secure their email. That changes today.
I will cover:
- Securing the machine you use email on
- Using a secure email service
- Securing your email account
- Using text only and not HTML
- Simple rules
I consider each of these an essential ingredient to securing your email. Once you have read this tutorial, you should be able to introduce each of these into your own email habits. Some you can use with your existing email accounts, others you won’t. How far you go with any of these steps is entirely up to you.
Secure the machine you use email on
Arguably the most important aspect of using email securely is making sure the device you use is secure. While important, it is rarely considered a risk. Yet it is the most significant risk. You could take all the precautions in the world and use the most secure email provider on the planet but if you have a keylogger on your device, all your efforts are for naught.
Regardless of the device type, the precautions you take are the same. Perform a virus scan regularly with a freshly updated, good quality virus scanner. If you use Windows, use Malwarebytes and perform a malware scan. The two scans look for different things so it’s important to perform both. Apple, Android and Windows all need antivirus scans to regardless of the device you use, keep them secure.
Keep your browser and operating system up to date. Many viruses, Trojans and malware target weaknesses or vulnerabilities within a browser or OS. Regular updates are released to plug these weaknesses so you should always keep your programs up to date. This is true for every electronic device you might use.
Use a VPN. You can use a VPN on desktop, laptop, tablet and mobile so there really is no excuse. Rather than sending your network traffic, including emails in the open, use a VPN. Virtual Private Networks create a secure encrypted tunnel between your device and the VPN gateway. From there it goes out into the internet. Whatever you do online, you should always use a VPN. Nobody can track you, your data is encrypted and it makes life exceptionally difficult for anyone watching.
Using a secure email service
While they like to tell you otherwise, Gmail and Outlook.com are not secure email services. They make try to keep your email safe from the outside but they aren’t shy of helping themselves to your data. For truly secure email, you have two main options, use a secure service or host your own.
Secure email services such as ProtonMail, Tutanota, Kolab Now or Countermail offer free or mostly free encrypted email. Each offers SSL encryption, little or no logging and are about as safe as it gets right now. ProtonMail for example is based outside the U.S. and it is alleged that even the NSA cannot break their encryption. How true that is I do not know but it’s quite a claim.
Hosting your own email address is very straightforward. All you need do is buy a domain name and basic hosting from a web host. It costs as little as $2 a month and will come with a number of email boxes using the domain you buy. Not only does it look cool to have your own domain name, you can encrypt it using SSL and lock everyone out of it.
While neither of these solutions are perfect, each will secure your email enough for most uses.

Securing your email account
When using an email account, you will usually log in using your email address and a password. Passwords are notoriously weak and can often be brute forced in seconds. I’ll show you how to generate a super-secure password and offer some best practices for using them.
To generate a secure password, you need to avoid dictionary words as they are what a brute force attack will use. It is much better to use a passphrase with a mixture of characters. Something that doesn’t appear in popular literature or media and not in any dictionary in any language.
I tend to suggest using a line from a song or movie to generate a passphrase. My example of choice is always a line from Sweet Child of Mine, ‘She’s got eyes of the bluest kind’. Take the first letter of each word in the line, SGEOTBK. Then add a special character to the beginning and end ‘@SGEOTBK!’. Then swap the O for 0 and the B for an 8 to become ‘@SGE0T8K!’. There is the basis for a very secure password. One you are unlikely to forget too which is quite important.
The other way to generate secure passwords and to make sure you don’t repeat passwords anywhere else is to use a password manager. I use LastPass but there are lots of other managers out there that do much the same thing. It can remember logins, generate ultra-secure passwords up to 24 characters in length and can even automatically log you in. The one thing you must do is use a secure password to lock down your password manager otherwise you defeat the object.
Finally, many email services offer two factor authentication to enable you to log in. Use it. You will log in using your email address and password as normal but will also have to complete an extra step. Usually this is to enter a code send via SMS to your cell phone but can be by other means too. This adds an extra layer of security to your email address that is very hard to overcome.
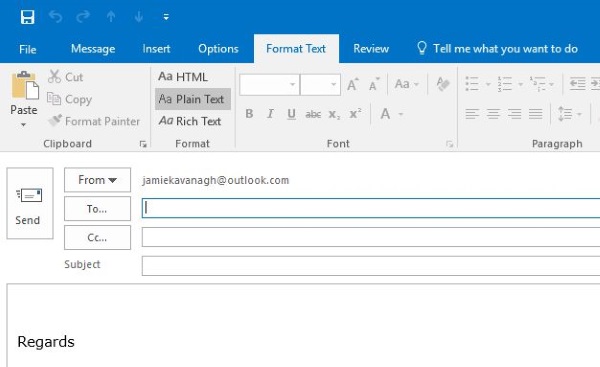
Using text only and not HTML
Using text only and not HTML does impact quality of life but will stop all malware, Trojans and anything nefarious hiding within an email from working. All email attack vectors use some kind of code to activate. Reading emails in plain text will either remove or expose that code and keep you safe.
It does affect the reading and writing experience but if you are truly concerned about email security, it is a logical thing to do. Most email platforms will have an option to read and use emails in plain text only. If you are truly concerned about security, use it.
Simple rules
Now you have secured your email as much as possible, there are some simple email usage rules you need to follow to maintain this level of security. They are basic but fundamental to internet security and everyone should follow them.
Never open attachments unless you know who they are from – If you can verify the sender and are expecting an email with an attachment, open it. In every other case, delete the email right away. If you don’t open the attachment, it won’t do you any harm as it will need some kind of user action to work, but delete it anyway.
Never click an email link unless you know who sent it – We have all seen spam emails and their various ways to get us to interact with them. Many are dumb and obviously phony but some are more sophisticated. Some look like they are from UPS or a credit card company. Never, ever click a link in an email unless you know who it is from. Hover the curser over the link if you’re curious. I bet you will see a destination that has nothing to do with what the link says!
Never reply to a spam message – You would be surprised at how many people respond to a spam message to tell the person to Foxtrot Oscar or to leave them alone. That is a mistake. While spam is sent by bots, every reply is logged and the email address is added to a real address list or suckers list. By replying, you have proven that your email address is real. Now the real spam targeting begins. Just don’t do it.
As you can see, while the subject of secure email is deep, the methods you can use to action it are straightforward. If you are concerned about email security or just want to keep private correspondence private, you now know how to do it. I hope it helps!