How Cell Phones are Cloned and How To Stop it From Happening To You

Cell phone cloning, while not as prevalent as it used to be, continues to be an issue for some mobile phone users. Cell phone cloning is a method, using electronic equipment, for criminals to steal the identity of a phone, hijack the carrier, and get free service for themselves.
This can be anything from a minor nuisance to a serious problem for the victim of cloning. The consequences range from having bogus charges appearing on one’s bill, all the way up to criminal charges being filed if a cloned phone is then used to commit a crime.
In this article, I will explain what cell phone cloning is, how it works, and what you can do to protect yourself against cell phone cloners.
How cell phone cloning works
Cloning a cell phone is a two-step process.
First, the crooks use an electronic scanner to detect the electronic identification number of the SIM card in a nearby phone. There are a variety of different kinds of scanners and they can be found on the dark web among other places; it isn’t our goal here to teach you how to clone a phone so I’m not going to link to any of the places where they can be bought.
Scanners are relatively expensive and difficult to get, but not impossible. Most phones have significantly enhanced security against cloning operations, a phone cloner is much more likely to try to get physical access to the SIM card. With physical access to the card, cloning is relatively easy to accomplish, especially for those on the GSM network where swapping sim cards between phones is simple.
Once the cloner has the information (usually consisting of the electronic serial number of the SIM card, and its authentication key), they will use a SIM writer to make a duplicate SIM card.
Because SIM writers are legitimate tools with many legal uses, they are easy and inexpensive to acquire, and anyone with $10 or $15 to spare can get one via eBay without any hassle. The cloner can then put the duplicated SIM card in another phone, and use that phone to make calls and connections under the original phone owner’s account.

It used to be much easier to clone cell phones than it is today. In the early days of cellular communication, both the phones themselves and the cell network that supports the phone operated on analog technology.
Now all cell phones are digital and their signals are encoded and encrypted, making it almost impossible to scan for SIM information. There is one weakness in the system, however, and that is the existence of analog backups.
In high-traffic areas, many carriers keep analog cell stations running to handle the overflow. When a single station becomes very busy, it overflows some calls to the old analog network. Someone with a scanner within range of that network can harvest your phone’s identifying information.
Analog systems used CDMA technology which transmitted your phone’s ESN (Electronic Serial Number) and MIN (Mobile Identification Number) along with the call data. Digital systems use GSM which shifted to using a phone’s IMEI.
The ESN and MIN used to be simple to flash, IMEI is slightly different. Now, they can capture IMEI data and use a hardware SIM reader and writer to clone the SIM, not the card.
The signs of a cloned phone
There is no easy way to tell that your phone has been cloned. If your friends and family and receiving phone calls from you, your phone number may have been “spoofed” meaning someone is using an application that mimics your phone number on caller ID. Your phone may have been hacked as well.
Tracking the location and activity of your phone is different from cloning. Here is an article to help you prevent your cell phone from being tracked.
However, there are a few telltale signs that may indicate your phone has been cloned, including:
- A call from your carrier asking if you have traveled.
- A sudden increase in calls or SMS messages from unknown or unfamiliar numbers.
- More wrong numbers or abandoned incoming calls than usual.
- Disappearing voicemails or difficulty accessing your voicemail.
- More and/or unusual call activity on your bill.
- Your phone suddenly stops making phone calls or connecting to the cellular network – this happens when someone duplicates a SIM card and puts it in a different phone.
If you do suspect foul play there are a couple of other things you can check.
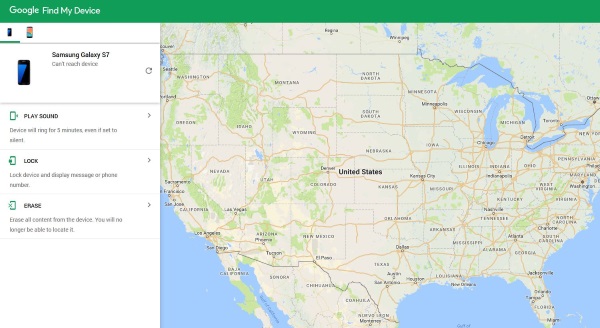
If you use Android, use Google Find my Phone to check your phone’s location. If you use iPhone, Find My iPhone to do the same. These are not exact, but they should at least offer a clue if your phone has been cloned by someone in a different country. However, this will only work if the location is enabled on the phone.
You can check your call and text log online with most carriers. This will alert you that there’s suspicious activity such as; phone numbers dialed that you’re certain didn’t come from your phone.
Talk to your carrier if you have suspicions. Although carriers do not track your phone or your activity, they can provide you with a new SIM card or direct you to an updated list of your call and text activity.
Preventing phone cloning
The most effective step you can take to prevent your phone from being cloned is not to let it out of your sight or let it fall into the possession of another person. Because of the enhanced security in the phone networks, it’s very difficult, bordering on impossible, for someone to effectively clone your phone just because you walk past their scanner.

Instead, they have to physically get their hands on the device so that they can pull the identifiers off the hardware or download a cloning application.
You should definitely secure your phone using a PIN number or a biometric (fingerprint) password so that if you lose your phone, someone else can’t get access to it. To prevent wireless interception of your information, turn off Bluetooth and WiFi when you’re not using them.
Don’t install suspicious apps that you aren’t 100% certain aren’t Cloneware. Cellphone cloning isn’t as prevalent as it once was, but it still happens. While there is little to do to completely prevent it, these basic precautions will lower the chances significantly.
How to Fix a Cloned Cell Phone
The first action you should take if you feel that your phone has been cloned is to get a new SIM card. Whether your carrier is on the CDMA network (Sprint and Verizon) or the GSM (AT&T and T-Mobile) network, updating the SIM card number within the carriers system means the hacker can no longer use your phone number.
It isn’t likely that someone can clone a cell phone that is attached to an eSIM. This type of SIM card is hardwired into newer smartphone models like the Google Pixel models and the newest iPhones. The only drawback is not all carriers have converted to the eSIM technology.
You can always buy a new cellphone, but changing the SIM card should suffice. It’s important that you shred or dispose of your old SIM cards properly. The CDMA network SIM cards are reusable but only compatible with your phone’s IMEI number once activated.
GSM carriers allow you to swap your SIM card between any model of phone, but once a new SIM is activated on your phone number, the previous one is disabled. This means that if you activate a new sim card, the old one will no longer work.



















30 thoughts on “How Cell Phones are Cloned and How To Stop it From Happening To You”
( dunenectarwebexpert .com)
( support ( @ ) dunenectarwebexpert ( . ) com)
(TeIegram @DUNENECTARWEBEXPERT)
What sapp Info: 1 (2 5 2 ) 3 7 8- 7 6 1 1
Thank you.
I was able to retrieve my psn gaming account after 2 months of being unable to login.
My account was stolen and i had a lot of funds and history on my account and couldnt just let it go,
So i decided to contact a hacker for help. I gave him my information and to my surprise he got back
my gaming account in 48 hours. I also gave him other jobs like hacking into my girlfriend phone to catch her cheating
and he always came through. contact (A C E T E A M H A C K E R S at G MAIL . C O M)
if you also need to hack into any gaming account.
I’ve been targeted since 2017 and how did I find out?
People started talking about my personal issue right after I talked to friends ON PHONE. They’re crazy a**hole. Been changing phone number and SIM card 4 times, didn’t work. They just keep digging. I ain’t having enough money and courage to track them down and get a redemption.
He linked himself to my accounts, has been downloading my data, photos everything. Messing with my apps, putting locations on, deactivating security apps and all. He has made threats to take my son and is involved with dangerous unstable people.
I can’t afford a new phone, and I’m in the middle of gathering evidence for court.
How do I get free and rid of him connected to my phone and accounts.
My x husband wife is in this deep she had someone kill my ropen horse she had these people set me up BUT that just got proven 10k later now they harrass me with drones..I don’t leave my ranch I’m up through the night cking all my horse’s.
I need some help please