Protect Your Browsing With DNS Over TLS
What is DNS Over TLS?
You already know that there’s been a lot of buzz in the last few years around encrypting web traffic. Even if you haven’t payed much attention, you have to have noticed the influx of green locks near URLs and HTTPS popping up everywhere. That’s because more sites than ever are encrypting traffic.
Encrypting web traffic protects both the site and the people visiting it. Attackers can’t easily spy on encrypted traffic as it passes between your computer and a website, keeping your login information and anything else you submit safe.
There’s one piece that doesn’t get encrypted by using HTTPS, the DNS query. If you’re not familiar, websites actually exist at an IP address. When you punch in the URL of a site, you make another request to a DNS server asking which IP address that URL belongs to. More often than not, that DNS server belongs to your ISP. So, they, and anyone else that might be listening in, can see which sites you’re going to and log them. Because DNS isn’t encrypted by default, it’s fairly easy for any sort of third party to be monitoring DNS queries.
DNS Over TLS brings the same type of encryption that you expect with HTTPS to DNS queries. So, the only person that receives your query and the data about which site you’re visiting is the DNS server that you choose, and you can choose. You don’t need to use your ISP’s DNS, and you shouldn’t.
What Can You Do?
Support for DNS over TLS isn’t as mature as HTTPS yet, but it’s still easy enough to get set up and use. There are a number of options that you can use to protect your DNS traffic. First, it’s worth noting that using a properly configured VPN will already protect you. Your DNS traffic will be tunneled over the VPN to the provider’s DNS servers. If you’re already using a VPN, don’t worry, though you can set up additional protection if you like.
If you aren’t using a VPN, you can still encrypt your DNS traffic with DNS over TLS. There’s an excellent open source project, called Stubby, that automatically encrypts your DNS queries and routes them to a DNS server that can handle DNS over TLS. Because the project is open source, it’s freely available for Windows, Mac, and Linux.
Set Up Stubby
Windows
Stubby has a convenient Windows .msi installer that will install Stubby along with a default configuration file. Head over to the installer page and download the Windows .msi installer.
Once you have it, run the installer. There isn’t a graphical setup wizard or anything. You only need to confirm that you’re giving the installer access. It’ll take care of the rest.
Everything for Stubby on Windows is located at:
C:Program FilesStubby
That includes the YAML configuration file.
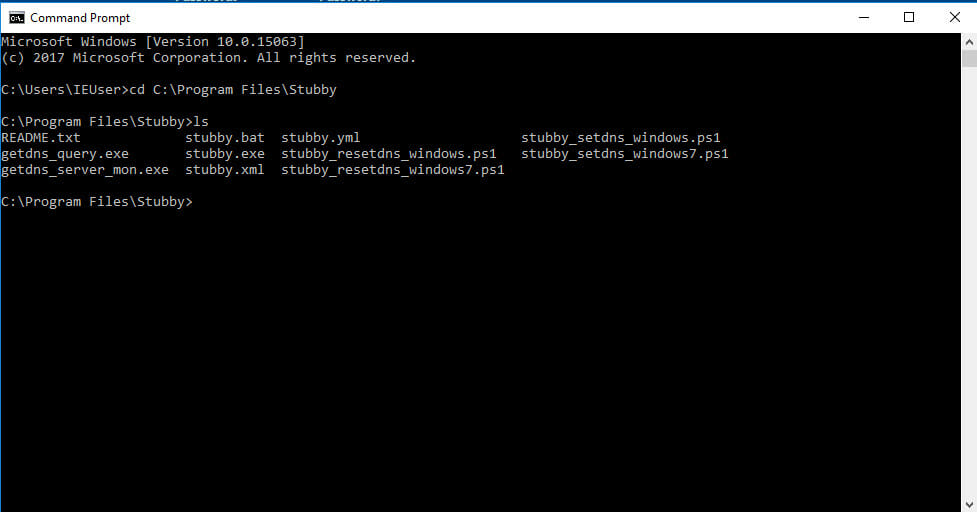
Open up a command prompt. You can use Run and type cmd. Change into the Stubby directory. Then, run the .exe and pass it the configuration to get Stubby started.
C:UsersUserNamecd C:Program FilesStubby
C:Program FilesStubbystubby.exe -C stubby.yml
Stubby will now be running on your system. If you want to test it out, run the following command to see if it’s running correctly.
C:Program FilesStubbygetdns_query -s @127.0.0.1 www.google.com
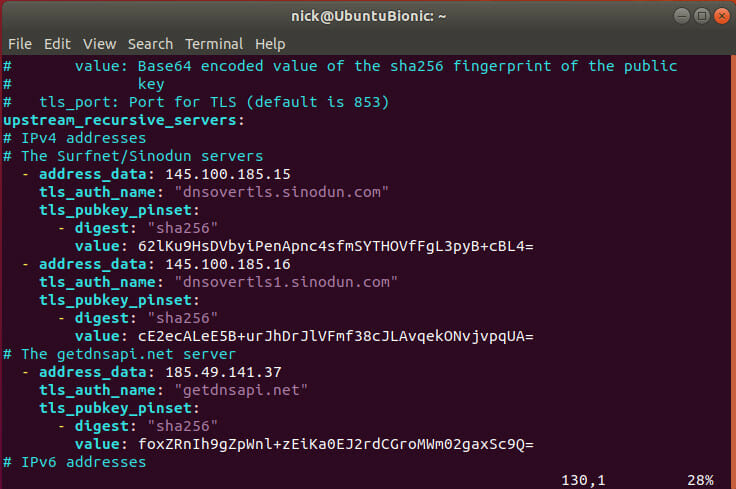
If that works, Stubby is set up correctly. Now, if you want to change the DNS servers that Stubby uses, open up stubby.yml, and modify the DNS server entries to match the servers of your choosing. Make sure that the servers that you pick support DNS over TLS.
Before you can use Stubby system wide, you’re going to need to modify Windows’ upstream resolvers(DNS servers). To do that, you’re going to need to execute a command with admin privileges. Close your existing command prompt window. Then, go back to your start menu and search for ‘cmd.’ Right click on it and select “Run as Administrator.” In the resulting window, run the following:
PowerShell -ExecutionPolicy bypass -file "C:Program FilesStubbystubby_setdns_windows.ps1"
None of this is very good if you can’t make the changes permanent. To do that, you’re going to need to create a scheduled task that runs on startup. Thankfully, the Stubby developers provided a template for that. In the running command prompt window you have, make your changes permanent.
schtasks /create /tn Stubby /XML "C:Program FilesStubbystubby.xml" /RU <you_user_name>
That’s all! Your Windows PC is now configured to use Stubby to send your DNS over TLS.
Linux
On Linux, this process is very simple. Both Ubuntu and Debian based distributions have Stubby already available in their repositories. You just need to install it and change your DNS to use Stubby. Start by installing Stubby
$ sudo apt install stubby
Next, edit the Stubby configuration file, if you choose. It’s available at /etc/stubby/stubby.yml. Open it in your favorite text editor with sudo.
If you’ve made any changes to the DNS servers, restart Stubby.
$ sudo systemctl restart stubby
You’re also going to need to change the nameserver entries in /etc/resolv.conf. Open that up with your text editor and sudo as well. Create a single entry like the one below.
nameserver 127.0.0.1
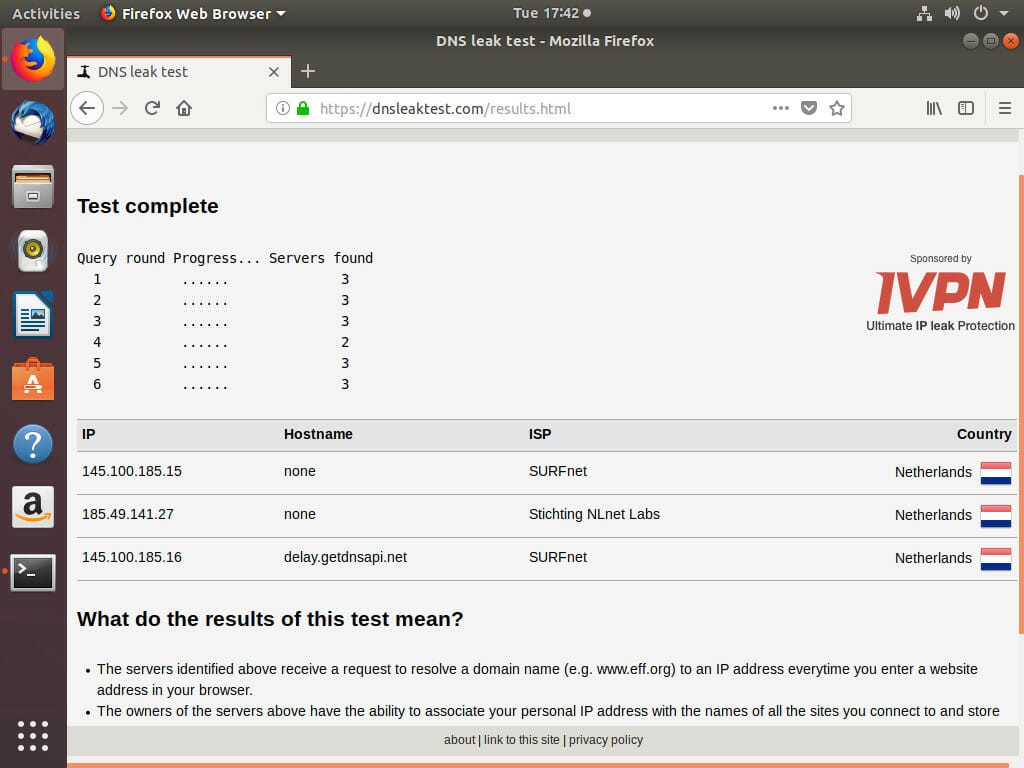
Now, test that Stubby is working. Go to dnsleaktest.com and run the test. If the servers that you configured Stubby to use appear, your computer is successfully running Stubby.
OSX
Setting up Stubby on OSX is also fairly simple. If you have Homebrew, the process is dead simple, but it’s also fairly easy otherwise.
With Hombrew, you can install the Stubby package.
$ brew install stubby
Before you start Stubby up as a service, you can modify the YAML configuration at /usr/local/etc/stubby/stubby.yml.
Once you’re happy with things, you can start up Stubby as a service.
$ sudo brew services start stubby
If you don’t have Homebrew, you can install the Stubby GUI. It’s available here.
Closing Thoughts
DNS over TLS is beginning to gain traction. Soon, it will be commonplace. Until then, setup and programs like Stubby are necessary. Clearly, though, it’s not too difficult to get set up.
In the near future, support for DNS over TLS will see a huge push forward when Google includes support by default with Android. As a result, it should only be a matter of time before Apple follows with iOS support. The desktop platforms probably won’t lag too far behind. Then again, they already do have support, and you just enabled it.