Can Google Photos Be Hacked?

In an ideal world, all apps and online services would be bulletproof and you wouldn’t have to worry about the integrity of your data. However, hacks plague online communities and you need to be aware of them to protect your information as much as possible.
On the bright side, Google and its apps and services are moving ever closer to making themselves bulletproof. But unless you’re careful, Google Photos might become vulnerable. Below, you’ll find out more about Google Photos security as well as some tips and tricks to help protect your account.
The Reason for Concern
Early in 2019, Imperva security specialist Ron Masas sniffed out a Google Photos bug devised to give hackers access to your personal information. Without going into technicalities, a hacker could take advantage of a Google Photos flaw to obtain the location, date, and user information contained within the photos.
The catch is to lure a user into accessing a malicious site while logged into Google Photos, then attack the system with a so-called XS-Search (Cross-Site Search). This hacking technique finds a way around the same-origin policy and abuses the time it takes for a browser to answer a query.
Put simply: a hacker could figure out what you’re searching for via Google Photos and pick up times, dates, as well as locations. Admittedly, this technique has its limitations, but experienced hackers incorporate other tools to boost XS-Search effectiveness.
The silver lining is that Google identified this and, effectively, patched the hole to keep your information safe. But this doesn’t mean you should let your guard down.

What Makes Google Photos Vulnerable?
Undoubtedly, the app itself offers great security. As mentioned above, the holes are quickly patched even if a flaw slips through the cracks. However, careless use of passwords, hotspots, and other apps can open doors for the big bad wolf. This is what you need to know.
Never Use the Same Password
This is the oldest trick in the book, but many users still use the same password for Google and their other accounts. For example, hackers utilize social engineering, clever thinking, and indirect methods to figure out the log-in information for Cloud-based apps.
Assuming you might be using the same password and username for other apps, the criminals test the information to determine if it works. Needless to say, your Google account is the first thing that comes under scrutiny.
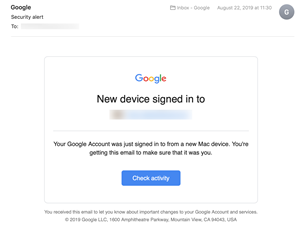
Luckily, you get an email whenever you or someone else logs in from a different device. It features a distinct layout and a button to check the log-in activity. Therefore, feel free to check out more details if you suspect something.
Avoid Using Hotspots
Apps and extensions such as Firesheep allow hackers to intercept unprotected cookies from websites like Twitter and Facebook. The good news is that Google account is mostly impervious to Firesheep, but there is plenty of other software that abuses public hotspot systems.
This kind of attack is called the “man-in-the-middle” and it confuses the public access point to allow one computer to be the main gateway. In turn, the hackers monitor all the traffic on that hotspot and everything that’s being sent, which may include the images you share or upload on Google Photos.
If you really like using public hotspots it’s best to get a VPN. It allows you to spoof the location and IP address, which basically hides your device in plain sight.
Limit the Number of Connected Apps
Google Photos integrates seamlessly with a number of third-party apps such as Shutterfly, for example. This provides for better user experience and allows you to use images directly from the Cloud service. But these apps still get full access to your Google Photos account.
So, what happens if your Shutterfly gets hacked? Chances are the Google Photos information will be exposed to cyber-criminals. This is particularly dangerous because they might be able to extrapolate enough data to gain access to all your accounts.
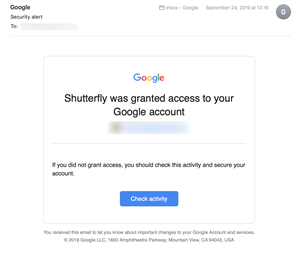
Judging by the email you get from Google, it’s super-important to keep track of the third-party apps you link to the account. And again, using different passwords and linking only the apps you use most gives you an upper hand. Truth be told, most apps work just fine even if you hit the Cancel button when they ask to connect to Google.
Advanced Data Protection Program
Even the best password won’t protect you against whaling and phishing attacks. The Advanced Protection program is engineered to eradicate the weak links that may occur in two-factor authentication. Case in point, push notifications and SMS authentication can fall prey to an experienced hacker.
To counteract this, Google deployed multi-factor authentication that combines physical keys and software locks. For example, if you want to make some major changes in your Google Photos account, you’ll be asked to use the fingerprint scanner to unlock the app. Therefore, if you haven’t set up Advanced Protection on your account, it’s not too late to do it now.
Hack the Hacker
The sad fact is that hack attacks don’t seem to be on the wane. But Google is still a step ahead of the criminals and one of the least vulnerable services. Nevertheless, you’re also responsible for keeping the account secure, so don’t forget to safeguard it.
Do you think your Google Photos have been hacked? Can you retrace your steps and tell us when and how it happened? Share your thoughts with the rest of the community in the comments section below.