Learn To Browse The Internet More Anonymously

Introduction
Protecting your privacy on the Internet is important. It isn’t just about not wanting others to see your activity. It’s about guarding your personal information and protecting yourself from being tracked by malicious parties.
Even though most people seem to think that hiding your activity is some sort of tinfoil hat thing, it isn’t that simple. By hiding your activity, you are making it harder for malicious hackers and identity thieves to find and target you. It’s also harder for advertisers to track and sell your browsing habits.
Really, when it comes down to it, hiding your online activity is just responsible practice.
Why Your Browser Matters
Not all web browsers are the same, and none are perfect. There are a couple of rules that do apply in nearly every instance.
First of all, always choose an open source browser. If a browser’s source code is freely available, you can see if it’s working as intended. That means, you know if it’s sending only your requests or it’s reporting back to the company that made it or outside advertisers. That may sound ridiculous, but it does happen.
It’s also important to pick a browser with the right configuration options and extensions. No browser is completely secure by default. If you can configure it yourself for maximum security there really isn’t a point.
With all of that said, there is no perfect browser. They all have strengths and weaknesses. Right now, though, the best option seems to be Firefox. It checks all of the boxes, and though there are some privacy concerns, they’re not nearly as major as on other browsers.
Configuring Firefox
Once you have Firefox installed, open it up and click on the three stacked lines in the upper right of the window. That will open up the main menu. Click on “Preferences.” Those are the main settings for Firefox.
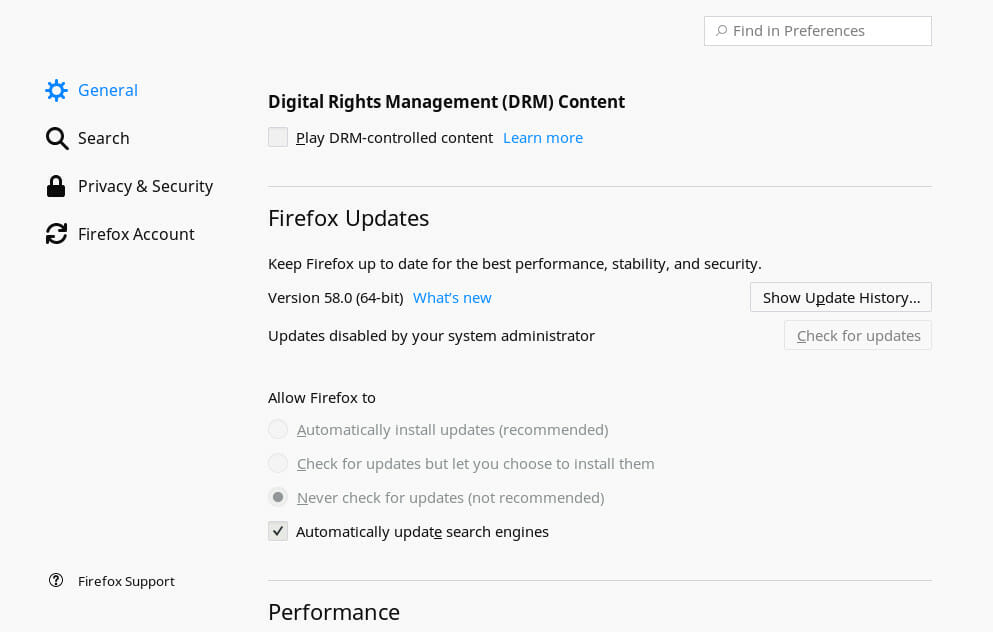
The first tab is the “General” settings. There isn’t much that you need to do, but you can uncheck the box for enabling DRM content. That probably doesn’t do anything, but DRM plugins are closed source, so you can’t say with absolute certainty what they do.
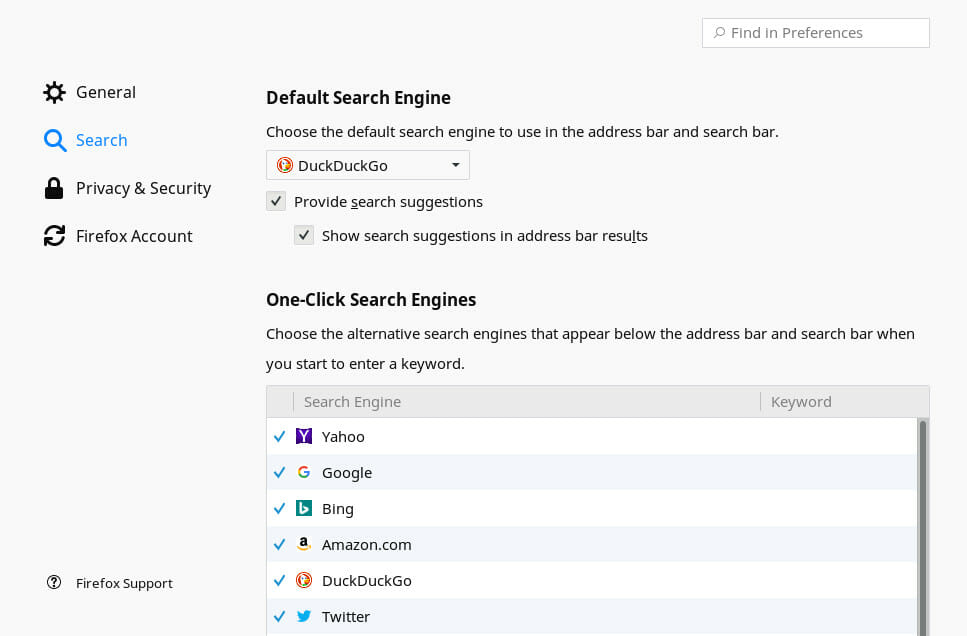
Next, move to the “Search” tab. Set either DuckDuckgo or StartPage as the default. Both are more secure than Google or Yahoo. Neither one tracks you by default.
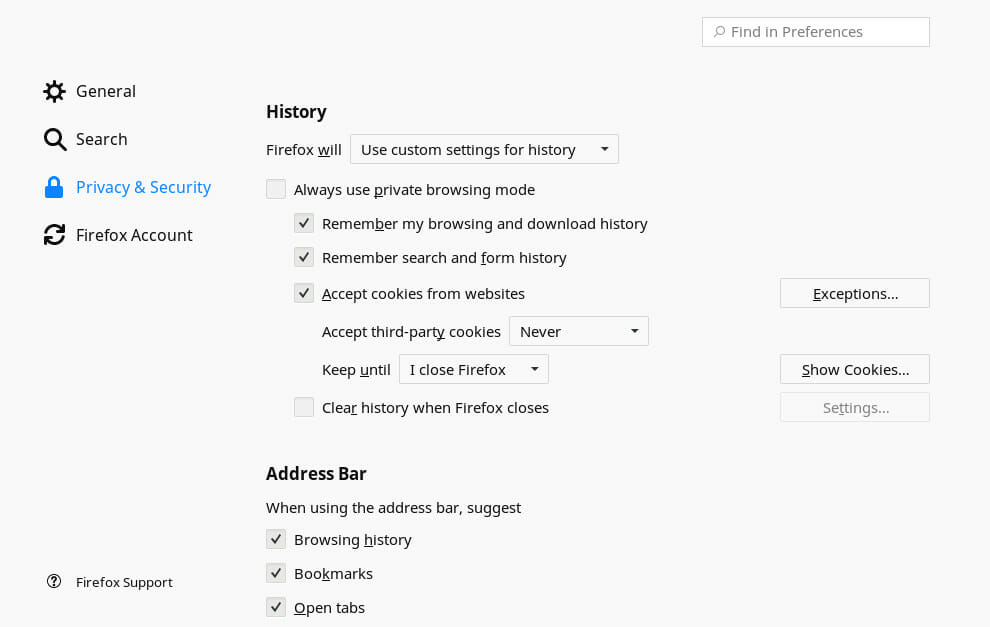
Head to the “Privacy & Security” tab next, and look for the “History” section. There you’ll find Firefox’s settings on cookies and browsing history. In the main dropdown, select the option to use custom settings. It’s entirely up to you how far you go with this. The minimum that you want to do is to never accept third party cookies.
Scroll down to “Tracking Protection.” Set both options to “Always.”
Move on to “Data Collection and Use.” Uncheck everything.
Finally, go down to “Security.” Check everything. That’s it.
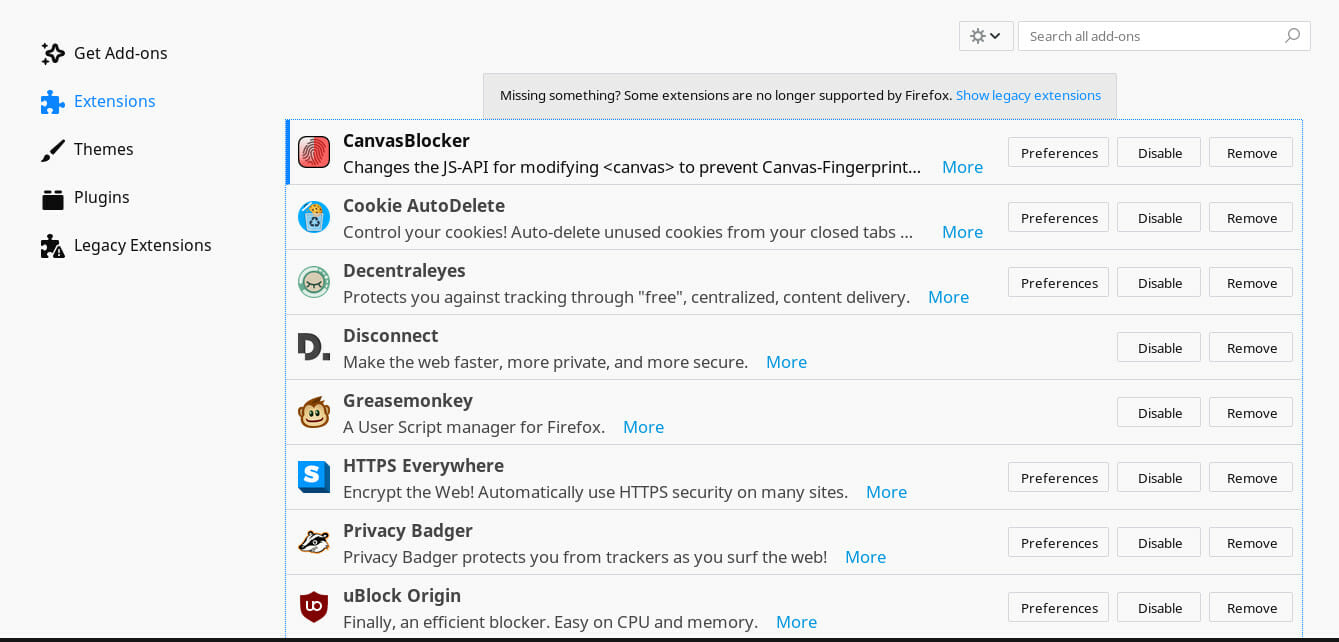
Extensions
While those settings are a step in the right direction, they aren’t perfect. There’s a lot more that can be done with Firefox extensions, and there are some really great ones available. They help to lock down and prevent common tracking methods.
HTTPS Everywhere
First up is HTTPS Everywhere. It was developed by the Electronic Frontier Foundation(EFF), and it forces all of your traffic to use the secure HTTP protocol instead of the unencrypted one. That makes it harder for third parties to interfere or snoop on your traffic. It doesn’t work on sites that don’t have an HTTPS version available, but now, most do.
Privacy Badger
Privacy Badger was also developed by the EFF. It’s actually similar to the “Do Not Track” protection offered by Firefox by default, but it amps it up. Unlike regular Do Not Track, Privacy Badger actively shuts down tracking and blocks additional forms of tracking. It really is an excellent tool for stopping unwanted trackers.
uBlock Origin
uBlock origin is an ad blocker, and it’s probably the best one available right now. That’s because it doesn’t just block ads. It actually blocks ad servers. So, instead of detecting the sizing of advertising banners and pop-ups, it flat out blocks the requests to the servers that they come from.
uMatrix
uMatrix is another add-on from the developer of uBlock Origin. It’s actually based on the same principles. Instead of just blocking ads, though, it blocks all external requests by default. Then, you can click on the icon and open up the matrix window. From that window, you can select which requests you would like to allow. It tells you where the request is coming from and what type of request it is. This way, you’re in complete control of what your browser is interacting with.
Cookie Autodelete
This one is fairly self-explanatory. Cookie Autodelete automatically deletes your cookies after you leave a site. This way, you can still access all of the sites that you want to, but they can’t follow you after you leave.
Disconnect
Disconnect is very similar to Privacy Badger. It isn’t strictly necessary, and you can leave it out if you choose. If you do want to add it in too, it provides an additional layer of protection against unwanted trackers.
Decentraleyes
Decentraleyes provides protection from a different type of tracking. So many sites rely on content delivery networks(CDN) to serve images, scripts, and other content. As a result, it may be possible to track someone across multiple sites based on the CDN that they’re connected to. Decentraleyes allows you to connect to local assets instead of the ones being served by the CDN, bypassing much of their tracking potential.
CanvasBlocker
HTML Canvas tracking is a real problem. Sites can use HTML5 canvas elements to uniquely identify your browser. The easiest way to handle it is by installing the CanvasBlocker add-on. Just by installing it, you’ll gain some protection. If you want, you can go into the setting and block all canvas tracking, but it’s not necessary.
Advanced Configuration
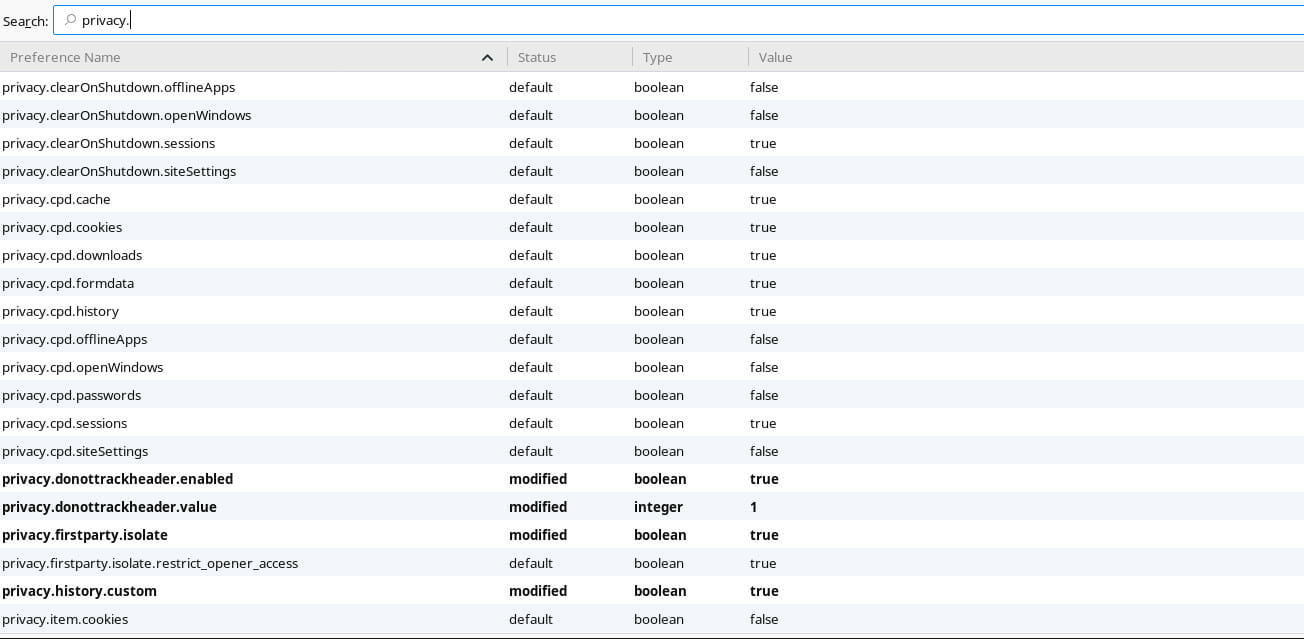
There’s yet another level of configuration that you can take to Firefox. Firefox doesn’t expose all of its settings through the regular menus. There are far too many options, and it’s very easy to break things. That said, you can access all of Firefox’s options by tyling about:config into the address bar.
Go ahead and open Firefox’s advanced settings. It’ll immediately tell you that you’re risking breaking Firefox. Don’t worry, and confirm that you wand to open the settings.
The advanced configuration comes in the form of a huge table. Each entry has a name, type, and value. It will also tell you if that setting has been modified. At the top of the table, you’ll find a search box. That makes navigation bearable.
The first set of settings is under the privacy section. Search for the following settings, and set them all to true.
privacy.firstparty.isolate true privacy.resistFingerprinting true privacy.trackingprotection.enabled true
Then, disable offline caching.
browser.cache.offline.enable false
Google provides a couple of security features, but they require you send data to Google. Clearly, disabling them is better for privacy.
browser.safebrowsing.malware.enabled false browser.safebrowsing.phishing.enabled false
There are a couple more settings that you need to account for in the browser section.
browser.send_pings false browser.sessionstore.max_tabs_undo 0 browser.urlbar.speculativeConnect.enabled false
A lot of this is here to limit what websites can see about you. In this case, stop them from seeing your battery levels and copy events.
dom.battery.enabled false dom.event.clipboardevents.enabled false
Disable geolocation
geo.enabled false
Limit the collection and behavior of cookies. These not only stop the browser from accepting some cookies, but they actually limit the amount of information that cookies can send.
network.cookie.behavior 1 network.cookie.lifetimePolicy 2
Set your cross origin request policy to limit the access from third party sites.
network.http.referer.trimmingPolicy 2 network.http.referer.XOriginPolicy 1 network.http.referer.XOriginTrimmingPolicy 2
WebRTC
WebRTC was originally designed to make sharing media easier. That means that it allows access to capture devices like webcams and microphones. It can also easily give away your actual IP address when behind a VPN. Disable WebRTC.
media.navigator.enabled false media.peerconnection.enabled false
WebGL
WebGL is used for rendering web graphics, like 2D and 3D games. Even though all of that is pretty great, it can also be used to track and fingerprint your browser. Disable WebGL.
webgl.disabled true webgl.disable-wgl true webgl.enable-webgl2 false
Using a VPN
For everyday use, a VPN is probably your best line of defense, next to your browser itself. They’re relatively inexpensive, and they prevent a lot of tracking methods. They also help to improve your security by obscuring your actual IP address and location.
What Is A VPN?
A VPN is a virtual private network. So, your computer joins the virtual network, and it’s almost like your computer is in two places at once, your actual network and the virtual one. When you connect to the internet through a VPN, it appears to every site that you connect with that your computer is located where the VPN is.
So, if you connect to a VPN server in Atlanta and connect to a website, that website will see your IP address as the IP of that server in Atlanta. It will also look to that site like your computer is there in Atlanta with the server.
There are VPN servers around the world, so you can bounce all around the globe with your VPN as you need to.
How Do VPNs Help?
VPNs hide your IP address and your location. They also mix your traffic in with thousands of other people. So, it becomes nearly impossible for a website to look at your traffic and trace your IP address and/or location directly back to your. The best they can do is see that your traffic is coming from a VPN server. Even if they knew that you used that VPN, they still wouldn’t be able to connect the dots between those pieces of information.
When you combine the modifications that you’ve made to Firefox with a reputable VPN, it would be very difficult for a website or even an attacker or identity thief to follow you. They probably won’t even know it’s you or that you exist at all.
Make no mistake, a VPN doesn’t make you anonymous. It just makes you hard to follow. Think of it as dressing like everyone else in a crowd.
Picking A VPN
Picking the right VPN is not easy. There isn’t one recommendation for everyone, and different VPNs work better for different people based on your location. There are some things to consider in every case, though.
First, look for VPN providers that provide a free trial. You’re going to have to try out a couple before you pick one that you like. It’s better to do it for free. Reputable VPN providers offer free trials because they understand the nature of the business.
Look at the number of servers that they provide and where those servers are. It’s not great to sign up for a VPN provider with only five servers. It also might not be great to sign up for one with thousands. A moderate amount of servers provides options while still retaining a deal of quality in most cases.
Of course, it’s also important to look at their privacy and security policies. Do they keep logs? They shouldn’t. A VPN provider should never log traffic or your logins. They shouldn’t track you at all. A good VPN provider will also post a warrant canary to let its users know if it’s been searched by a government agency. A warrant canary is usually a simple notice saying that they haven’t been searched. It’ll disappear should something happen.
It’s also a good idea to take note of where your VPN provider is based. Generally, for privacy, it’s a good idea to avoid services based out of the US, UK, Canada, Australia, and New Zealand. They members of the digital spy alliance known as the Five Eyes and have the most invasive anti-privacy laws.
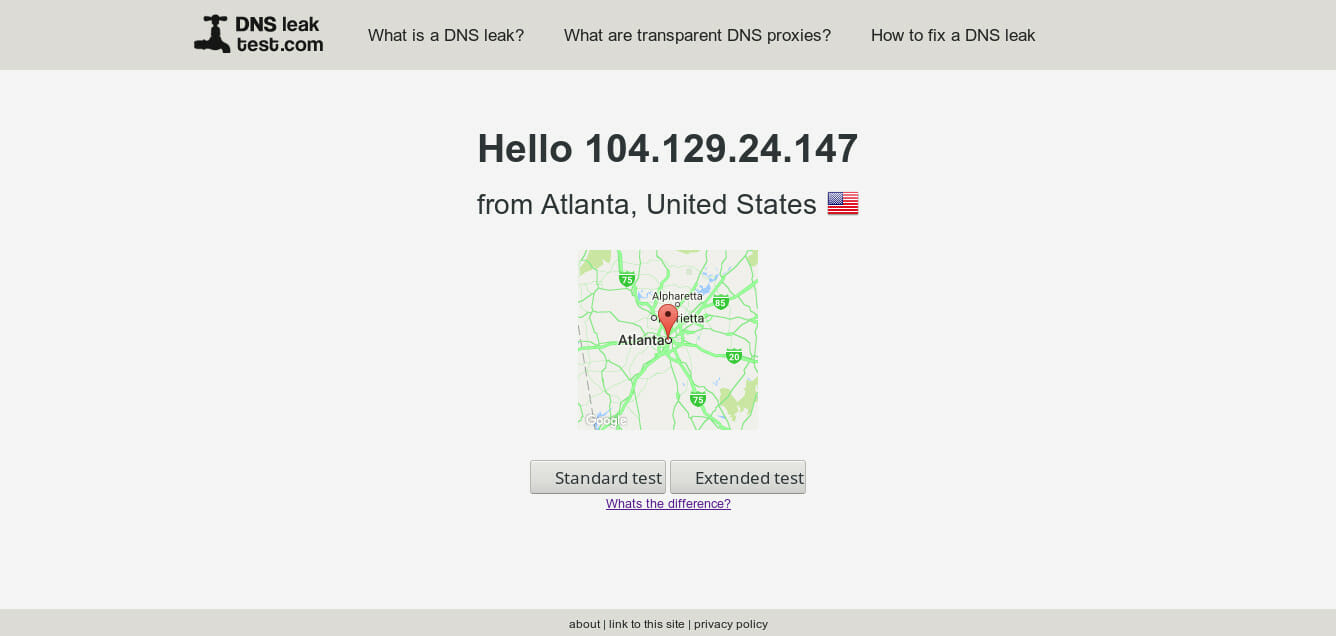
Testing For Leaks
Once you have your browser configured and you’re connected to a VPN, you need to make sure that everything is working. There are a number of sites out there to test that your VPN is actually working and your real IP address isn’t leaking. Check out dnsleaktest.com to see if your IP is leaking from a DNS server. For a more advanced leak test, try doileak.com. If you’d prefer to test individual privacy threats, check out browserleaks.com. If you’re going to be using torrents over your VPN service, try ipmagnet.
You should run multiple tests to make sure that you are actually reasonably well protected when browsing. Nothing is perfect, but the more tests you pass, the more sure of yourself you can be.
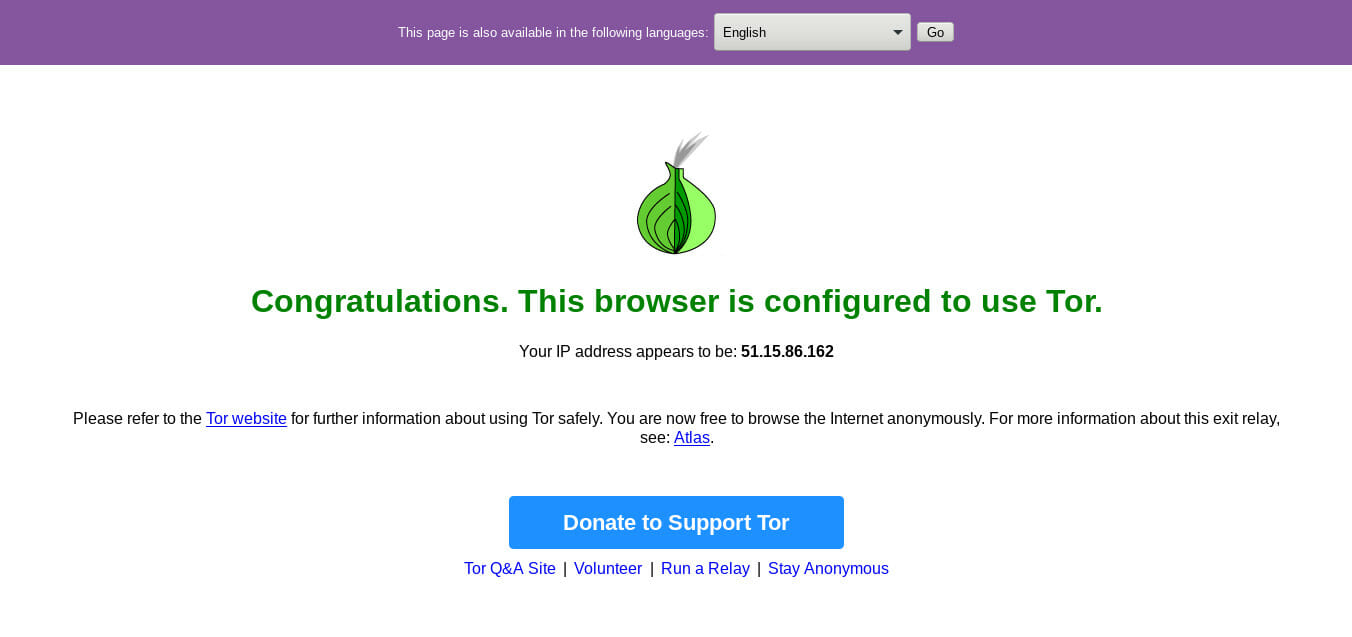
Tor
While the combination of a well configured browser and a VPN is great for daily use, you may want something for a higher degree of anonymity. In that case, Tor is the answer. Tor is a different type of networking protocol that bounces your connection across multiple nodes across the globe. Each node only has part of the connection information, so it’s very difficult to trace Tor traffic back to its origin(you). Because Tor traffic makes multiple bounces before it reaches its destination, it is generally very slow. That’s why Tor isn’t for regular use. It should be reserved for more extreme privacy concerns.
Tor comes from the non-profit Tor Project, and it is an open source project. You can set up your own Tor server locally, but the easiest and most secure way to use Tor is with the browser bundle. You can download the Tor browser bundle directly from the project’s website. It comes with a simple executable that you can just run. It automatically connects over Tor. The browser itself is based on Firefox, so it’s nothing confusing or alien to use.
Final Notes
Privacy and security are moving targets. Everything is always changing. Don’t expect everything that you read hear to remain true indefinitely, so stay vigilant.
It’s also important to remember that nothing is perfect. These measures just make it harder for your to be tracked, not impossible. Always ask yourself what your threat actually is. If you’re just trying to avoid advertisers, malware, and identity theft, these measures are probably overkill.
It’s always alright to modify the settings detailed here to suit your own tastes too. If something breaks more sites than it’s worth, you can certainly disable it. The point of all of this here is to put you in control.