What Is a DDoS Attack?

A DDoS attack is something you can hear or read about in everything from gossip magazines to specialty developer forums. It’s a common nuisance that’s been around since the late 90s which plenty of hackers or even disgruntled employees may use to cripple a system from a remote location.
Here’s what you need to know about how a DDoS attack is launched, what it does, and how big are the potential implications on an unsuspecting or unprepared target.
DoS vs. DDoS
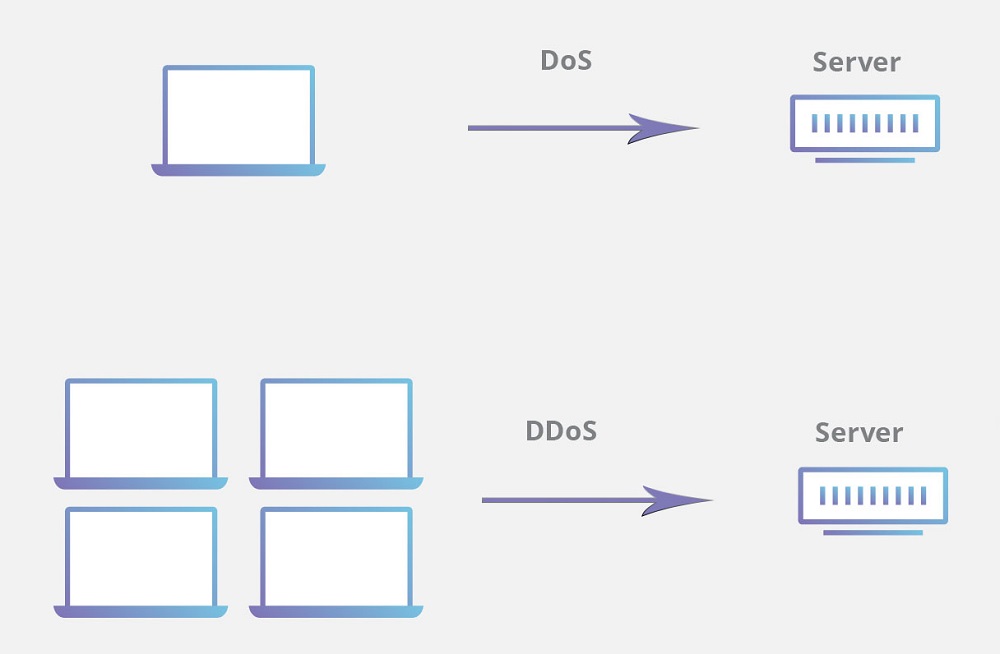
The term ‘DoS’ stands for denial-of-service attack. This cyberattack involves limiting or disrupting the services of a host.
The most common way in which this is achieved is by flooding the host with superabundant requests. This causes an overload on the target’s machine and can also make it non-responsive to most if not all legitimate requests from other users.
A DDoS is basically a DoS attack on a much larger scale. It is also referred to as a distributed denial-of-service attack. The same flooding technique is used on the target machine but it comes with a twist.
DDoS attacks have multiple origin sources. Therefore, it is increasingly difficult to prevent them. A DoS attack can be stopped by blocking the source, but in the case of a DDoS attack it’s not as simple as a basic ingress filtering will not be effective.
DDoS Implications
- Inability to distinguish legitimate users
- Website unavailability
- Slow network performance
- Increased number of spam emails
- Internet services denial of access
- Disconnection from wired or wireless internet connections
- Crashing hardware
Common Attack Tactics
IP spoofing is one of the most common DDoS methods. Creating fake IP addresses makes it even harder to find and block the original sources of the attacks.
Botnets are also a trademark of DDoS attacks. If you don’t know what a botnet is, think of it as a network of computers which act like sleeper agents. The computers receive commands to attack a certain host or target system.
Often times these machines receive and execute the orders without the owners ever knowing about it. This makes DDoSing extremely powerful as the potential to expand the network is quite high. It also prevents hosts from simply adding more bandwidth to deal with the problem.
Intended Use
Many DDoS attacks are used in extortion schemes against financial institutions or business owners. The attackers usually start out small with a simple DDoS attack as a proof-of-concept. The targets are then made aware of the vulnerability in the system and are prompted to pay out a fee.
Most payment requests are in Bitcoin or other alternative virtual currencies that are notoriously hard to trace back to the attackers.
Some DDoS attacks are intended to damage the hardware components of the target system. This is called PDoS, permanent denial-of-service or phlashing.
PDoS involves taking remote control over the management of the target system’s hardware devices which include but are not limited to printers, routers, and most networking hardware. The attackers use modified or corrupt firmware images to replace the original firmware of a target piece of hardware.
After one of these attacks, the system may be damaged beyond repair. This means that the target may have to replace all equipment. This costs time and money.
PDoS attacks are hard to notice. They can also be carried out without relying on a botnet or root servers.
Unintended DDoS
Sometimes the cause of a website overload may just be a surge in popularity. If thousands or hundreds of thousands of people all click the same access link to a website at the same time, the administrators might see it as a DDoS attempt.
Granted, this usually only happens on less prepared websites or new websites with limited bandwidth. It some circles, a variation of this is VIPDoS. The VIP stands for celebrities that can post links that attract thousands of clicks within seconds.
Prescheduled events may also cause a temporary denial-of-service. This happens because given enough time in advance, potentially millions of people know they have a limited timeframe in which they can benefit from a service.
For example, this type of unintended DDoS happened during the 2016 Australian census.
DDoS Protection
While there are several defense techniques that protect or mitigate the damage done by a DDoS attack, the best defense system involves using multiple layers of defense.
To be as well-prepared as you can be, you have to start by acknowledging that an incoming DDoS attack is a possibility. Combine attack detection, traffic classification, real-time response tools and hardware protection to have a higher chance of deterring an attack.
A high bandwidth is also important as even with advanced security measures it can be impossible to stop a 100GB DDoS attack on a 10GB bandwidth.
Commonly used DDoS prevention methods involve:
- Firewalls
- Intrusion prevention systems (IPS)
- Application front-end hardware
- Blackhole routing
- Routers
- Switches
- Upstream filtering
A Final Thought
Although more and more defense mechanisms and tools are continuously being refined, the number of DDoS attacks is still increasing all over the world. Some countries try to deter potential attackers by suggesting jail time a punishment.
However, very few countries actually issued well-defined laws regarding this. The UK is one of the few that has clearer guidelines when it comes to dealing with DDoSing. There’s a maximum 10-year prison sentence that can be given to anyone caught DDoSing. It’s also the only country that clearly defined DDoSing as an illegal activity.
The popular hacker group Annonymous has been lobbying to classify a DDoS attack as an accepted form of protest instead of an illegal attack. Do you think they’re right or is DDoSing too dangerous in the hands of those with bad intentions to be considered legal?