How To Setup WPA2 Enterprise on your Network

The most important aspect of any internet setup in 2019 is your wireless network. While wired connections are faster and often more secure, with the litany of devices lying around your house requiring a wireless signal. From smart TVs and speakers to your smartphone and tablet, a wireless connection is simply a must-have in 2019.
Of course, when it comes to wireless internet, you’re going to be dealing with a lot of different security terms you may not be familiar with, leading to plenty of confusion surrounding the wireless networking space. There are acronyms everywhere and loads of options, with most of these dealing directly with security protocols. All of this means your network security is directly at risk unless you know exactly what you’re doing.
So, for this article, we’ll be taking a look at WPA2 Enterprise security, how it works, and whether you need it. From the history of WPA as a security protocol to how WPA2 Enterprise can truly buff up your home security, this is your guide to setting up WPA2 Enterprise on your network.
What is WPA2?
 Wi-Fi networks started to pop up in the late 90’s as laptops became more popular and less expensive. At that time, WEP (Wired Equivalent Privacy) was developed in an attempt to do just what its name suggests; provide an equivalent level of privacy to wired networks. It fell way short, flat on its face. Then it burst into flames. Seriously, WEP is well known for being terribly insecure.
Wi-Fi networks started to pop up in the late 90’s as laptops became more popular and less expensive. At that time, WEP (Wired Equivalent Privacy) was developed in an attempt to do just what its name suggests; provide an equivalent level of privacy to wired networks. It fell way short, flat on its face. Then it burst into flames. Seriously, WEP is well known for being terribly insecure.
In response to the security disaster that was WEP, the WiFi Alliance developed WPA (WiFi Protected Access.) Since WPA was a direct response to WEP, it solved many of WEP’s many problems. WPA implemented TKIP (Temporal Key Integrity Protocol), which greatly improved wireless encryption by dynamically generating keys for each packet transmitted. WPA also includes checks to ensure that transmitted data hasn’t been tampered with.
While WPA was good, it also has its flaws. Most of them originated from the use of TKIP. TKIP was an improvement over WEP’s encryption, but it still is exploitable. So, the Wi-Fi Alliance introduced WPA2 with mandatory AES (Advanced Encryption Standard) encryption. AES is a stronger encryption standard with support for 256bit encryption. As of now, WPA2 with AES is the most secure option.
What’s The Difference Between Enterprise and Personal?
Now, there’s still that question of WPA2 Enterprise. After all, that is probably why you clicked on this article in the first place. If you’ve looked at the configuration settings of a wireless router made after 2006, you may have noticed that there two options for WPA2. On most routers, you can find one labeled, “Enterprise,” and the other is marked, “Personal.” Both options are WPA2 and use the same AES encryption. The difference between them comes from how they handle connecting users to the network.
WPA2 Personal also goes by WPA2-PSK or WPA2 Pre-Shared Key because it manages connections to the network with a password that has already been shared with the person connecting. This works well for small home networks because you can generally trust everyone on the network, and they aren’t much of a target for potential intruders. Chances are, if you’ve connected to the WiFi at a friend’s house, or set up your own wireless network, it was configured with WPA2-PSK.
WPA2 Enterprise is obviously focused more on business users. Instead of just using a single password for authenticating access, WPA2 Enterprise relies on a RADIUS server and a database of separate client credentials for authentication. This is great for businesses because they have the resources to set up a server for authentication. Businesses also have greater security needs. A business can also quickly recover in case a device is lost or stolen by assigning each user their own login information. Additionally, it allows a business to protect themselves against disgruntled employees who might want to harm their network.
What Are The Advantages Of WPA2 Enterprise?
The advantages of WPA2 Enterprise aren’t exactly advantages for everyone. If you’re just looking to set up a simple home network with little hassle or maintenance required, WPA2 Enterprise isn’t going to be a good solution for you. It’s pretty much the opposite of what you want. However, if you’re running a business, or you’re looking for fine-grained security on your home network, WPA2 Enterprise has several characteristics that make it an excellent candidate.
WPA2 Enterprise makes use of a database. While it might not be a big deal when you’re only dealing with a handful of users, having the power and utility of a database can be crucial when working with a large number of connections. It enables network administrators to track, manage, and manipulate data easily with tools that they are familiar with in an efficient way.
Using a database also helps to enhance another key characteristic of WPA2 enterprise networks, the ability to disable users’ credentials. A network administrator can easily disable a user’s account in case a device is lost, stolen, or that user leaves the company. Individual login credentials also help to contain potential threats by making it simple to remove any compromised machine from the network.
WPA2 Enterprise eliminates the need to change login information when an admin removes a user from the network or a single machine is compromised. It would be a massive pain for the IT department of a large corporation to have to re-connect each device on their network with a new login every time someone left the company. That just doesn’t make sense.

The use of individual user authentication keys also compartmentalizes the network, restricting what network data each user has access to. In a WPA2-PSK network, every user can see the network data of every other user. This makes it very easy for an intruder or would-be attacker to gain access to more information on the network and cause more damage. For enterprise networks, this is not a problem, thanks to the individual keys.
Another great feature of WPA2 Enterprise is the ability to use certificates for authentication. Passwords are problematic for so many reasons, not the least of which is their vulnerability to dictionary attacks. To make matters worse, it’s almost impossible to rely on your users to create strong passwords. It’s almost like people instinctively choose garbage ones every time. This is actually the greatest risk to WPA2-PSK networks. Certificates are almost like an insurance policy against bad passwords. Even if an attacker is able to guess a user’s awful password, they still won’t be able to log in without that user’s certificate. Certificates provide yet another layer of protection to enterprise networks.
How Do You Implement A WPA2 Enterprise Network?
It’s absolutely impossible to cover every possible configuration and combination of circumstances that can go into setting up a WPA2 Enterprise WiFi network. No one is going to have the same network hardware and software, and no one is going to have the same clients. There are, however, basic steps that network admins can use on every network setup.
Before you dig into the network itself, set up your user database. It might seem like overkill, but MySQL or a compatible clone like MariaDB is the best option. You can set up your database on its own machine, an existing database server, or on the same machine as the RADIUS server. Where you choose should depends on how big the database will be and how you plan on managing it. MySQL has proven itself fast and reliable. It’s also open source and compatible with whichever server platform you choose.
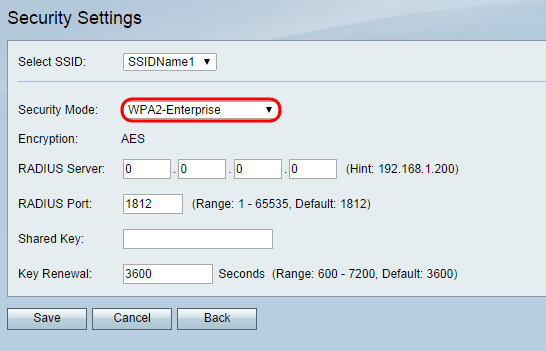
The RADIUS server is at the heart of WPA2 Enterprise. It is the main factor that differentiates enterprise networks from personal ones. RADIUS is responsible for managing connections and authentication. It also coordinates everything going between the router, the database, and the clients. There are a number of options for setting up a RADIUS server. In some cases, a router has RADIUS built in. There are also a number of commercial options to choose from. FreeRADIUS is an excellent open source RADIUS server that can be deployed on Linux, Windows, and Mac based servers. In any case, you’re going to have to configure your RADIUS server to connect to and use your MySQL database.
You’re going to need some keys. Encryption keys are obviously an important component in this whole equation. Again, there are a number of ways to approach generating your keys and establishing a certificate authority. On nearly any operating system, OpenSSL is a great option. OpenSSL is also an open source program that’s compatible with just about any platform.

With both servers configured and running and your keys generated, you can finally set up your router. Every router is different, so it’s not easy to go into specifics here. Just make sure that you switch your router’s wireless settings to WPA2 Enterprise with AES encryption. You will also have to provide your router with information to connect to your RADIUS server.
Finally, you can start connecting clients. Create client credentials and exchange keys. Connecting each client is going to be different. Every operating system and device handles connecting to networks and managing connections differently. Generally speaking, you’re going to need your certificates and the login information that you’ve already created. Be sure to configure the client devices to connect automatically to save future hassles.
So, Do I Switch?
Depending on who you are and what you need your network to do, switching may be a good idea. If your network is configured to use WEP or WPA currently, switch to WPA2 now! Don’t wait. Just do it. If you’re using WPA2 Personal, and you’re thinking about jumping over to enterprise, it isn’t as clear.
Don’t switch to WPA2 Enterprise if you’re a home user and you don’t know anything about databases or running servers. You will just end up frustrated with a broken network. Stick to WPA2 Personal and select a strong password. You’ll be much happier with it.
If you’re running a business and have employees, switching over to enterprise WiFi might be the right move for you. Just be sure that you are prepared and have all of the parts and pieces in order before taking the leap. Proper configuration is just as important to security as picking the right encryption and WiFi standard.
















3 thoughts on “How To Setup WPA2 Enterprise on your Network”
and i don’t know what is that use…… and pass and android also asks me for anonymous identity
and identity and password what all of these